Dyre Wolf malware huffs and puffs at your corporate bank account door

Dyre Wolf is not your usual malware campaign. These attacks, based on the Dyre banking Trojan, are ripping off companies for $500,000 and $1.5 million per attack.
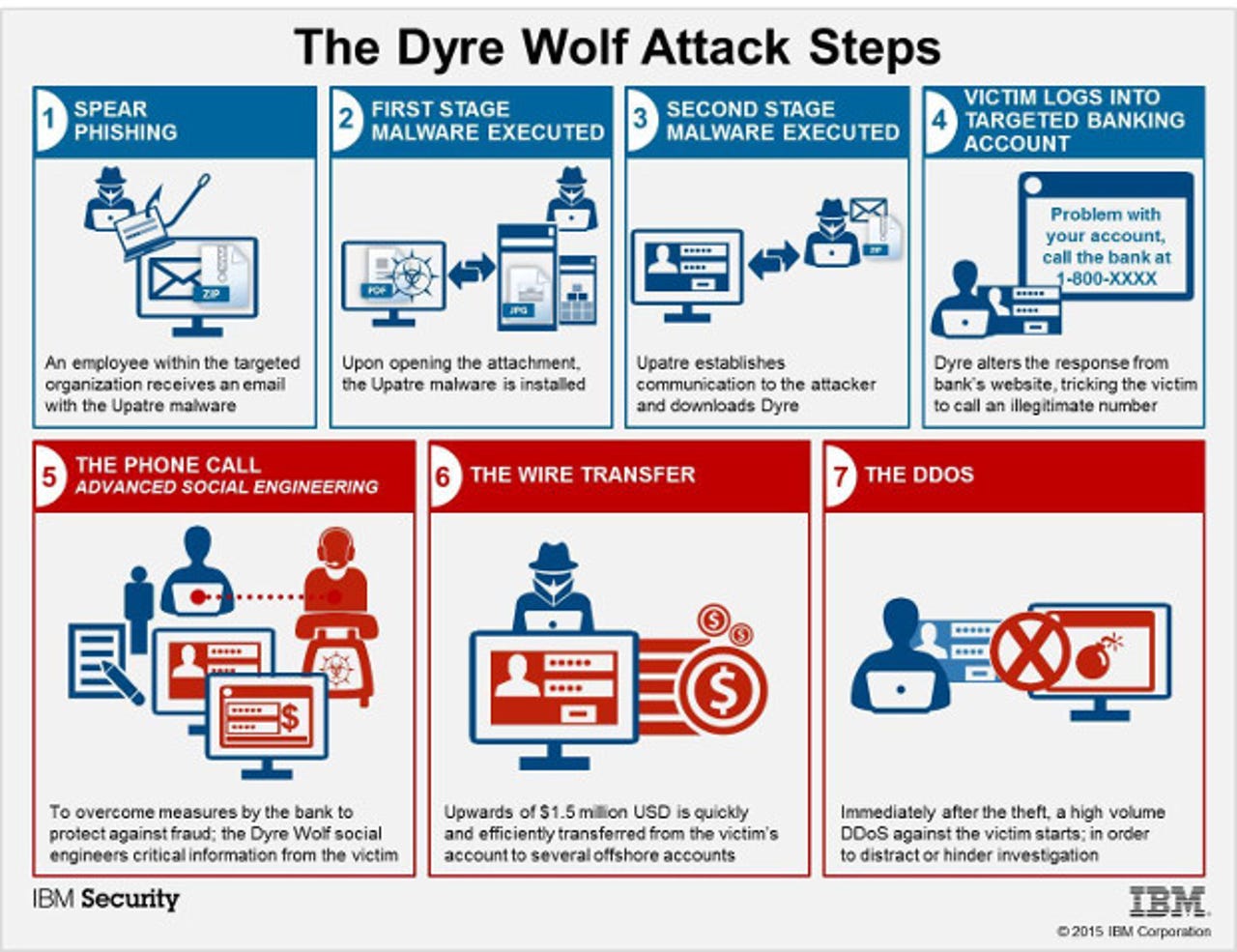
While most banking Trojans target individuals, the Dyre Wolfe attack isn't interested in the small fry. No, from the start, Dyre's been used to attack big corporations. What's difference now is that it's being used specifically to target organizations that frequently conduct wire transfers with large sums of money and it's doing so with humans involved in the attack.
Here's how it works.
First, Dyre starts to pry its way into your organization by appearing in your users' Outlook inboxes as an e-mail with an attachment claiming to be a fax or a package tracking notification. What's actually in there is Upatre. This program's only purpose is to download the far more malicious Dyre Trojan.
Once Drye is downloaded, it will try to spread itself to your co-workers and friends via Outlook. Then, Dyre will watch your work and wait for you to log into one of the hundreds of bank websites which Dyre is programmed to monitor.
Security
Now, it gets interesting. When you try to log in into the site, Dyre puts off a message stating that your account is having issues and that you must call the number provided to help you log in.
This part of the attack will happen regardless of your web browser. Chrome, Firefox, and Internet Explorer have all been spoofed with these fake pages.
If you call that number, you'll find, not an automated voice system, but a live person who will "help" you.
Yes, this is "computer" malware that actually uses people as part of its attack. Further, when you call, the crook on the other end of the line will be ready for your call. So, for example, you might be told, "Hi, I understand that you're having trouble with your bank account at Umbrella Corporation Credit Union, could I have your user ID?"
If you go along with this "helpful" person, when you're done, you really will be done at your current job. That's because the crook on the other end of the phone will have started a money order from your company's account. "The use of a live phone operator is what makes the scheme unique," said Caleb Barlow, IBM Security's vice president, in a statement.
Then, while your funds are being bounced from bank to bank to hide the money trail, your company's website will be subjected to a Distributed Denial of Service (DDoS) attack. The idea seems to be that your IT and security people will be kept too busy dealing with it to look for a rogue financial transaction.
So, what can you do about this? Well, there's the usual anti-viral remedies, but this is really more a matter of making sure your people, rather than your software, know how to do the right thing.
IBM Security recommends the following steps:
- Train employees on security best practices and how to report suspicious activity.
- Consider conducting periodic mock-phishing exercises where employees receive emails or attachments that simulate malicious behavior. Metrics can be captured on how many potential incidents would have happened had the exercise been a real attack. Use these findings as a way to discuss the growing security threats with employees.
- Offer security training to employees to help understand threats and measures they can take to protect the organization.
- Provide regular reminders to employees on phishing and spam campaigns and that they shouldn't open suspicious attachments or links from both work and personal emails.
- Train employees in charge of corporate banking to never provide banking credentials to anyone. The banks will never ask for this information.
Some people will still get it wrong. Some people will always get it wrong. That's why these kinds of attacks keep working year after year. But at least you'll have a better chance than before of keeping your company from losing a cool million from a single phone call.
Related Stories: