Google opens up on Titan security: Here's how chip combats hardware backdoors

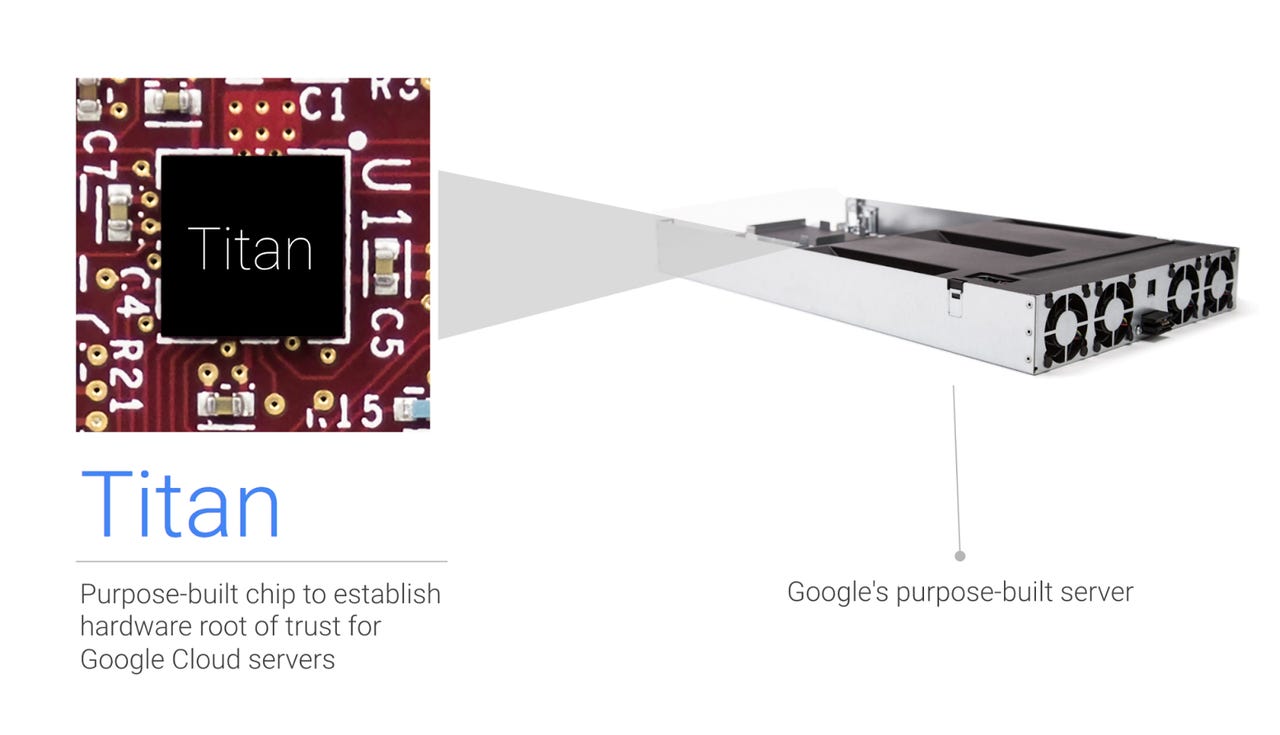
Google says it designed Titan's hardware logic inhouse to reduce the chances of hardware backdoors.
Google has detailed how its custom Titan security chip will prevent threats that use firmware-based attacks.
When it unveiled its tiny Titan chip, Google said it planned to use the processor to give each server in its cloud its own identity.
Security
Now, it's provided a more detailed rundown of what that means and how Titan will serve as a "hardware root of trust" to ensure each machine's firmware is safe to load and provide other cryptographic functions in its data center.
The chip's role is to thwart the type of attacks where, say, government spies intercept hardware and insert a firmware implant. Attackers are also exploring firmware vulnerabilities to overcome operating system defenses and install rootkits that can persist even after the operating system has been reinstalled.
"Google designed Titan's hardware logic inhouse to reduce the chances of hardware backdoors," Google Cloud Platform engineers wrote in a blogpost.
Titan comprises a "secure application processor, a cryptographic co-processor, a hardware random number generator, a sophisticated key hierarchy, embedded static RAM (SRAM), embedded flash and a read-only memory block," they added.
The chip scans the CPU and other components to monitor "every byte of boot firmware" and executes code from its read-only memory when a server is switched on. It also checks whether firmware has been tampered with.
Titan's boot memory uses public key cryptography (PKI) to verify its own firmware before loading it, and then uses PKI to verify the host system's firmware. Google's verified boot firmware then configures the machine and loads the boot loader and the operating system.
According to Google, these checks go beyond what would normally happen under Secure Boot, which verifies firmware on startup, since it can also patch Titan firmware and identify the first bytes of code that run at startup.
Google also detailed how Titan serves to give each machine its own cryptographic identity, which also helps it patch Titan firmware when necessary.
"The Titan chip manufacturing process generates unique keying material for each chip, and securely stores this material -- along with provenance information -- into a registry database. The contents of this database are cryptographically protected using keys maintained in an offline quorum-based Titan Certification Authority (CA).
"Individual Titan chips can generate Certificate Signing Requests (CSRs) directed at the Titan CA, which -- under the direction of a quorum of Titan identity administrators -- can verify the authenticity of the CSRs using the information in the registry database before issuing identity certificates."
This system allows Google's back-end systems to provision keys to Titan-enabled machines, as well as sign audit logs in a way that shows whether they've been tampered with, even by a malicious insider with root access to a machine.
Related coverage
Google Cloud unveils its custom security chip, new security features
Google Cloud adds firewall to App Engine
The aim is to give developers and admins a way to test and secure cloud apps. The App Engine firewall is in beta.
Read more on Google
- Google Home now lets you shop at Walmart using your voice
- Google launches Chrome Enterprise, aims to integrate with more business systems
- Google reveals official name of Android O
- Google Docs: This big update just added some serious new features
- Google Maps and mobile search gain Q&A for business listings
- Google Assistant: The smart person's guide (TechRepublic)
- How to get started with a Google-powered smart home (CNET)