Ransomware email campaign targets government staff with lure of cheap flights

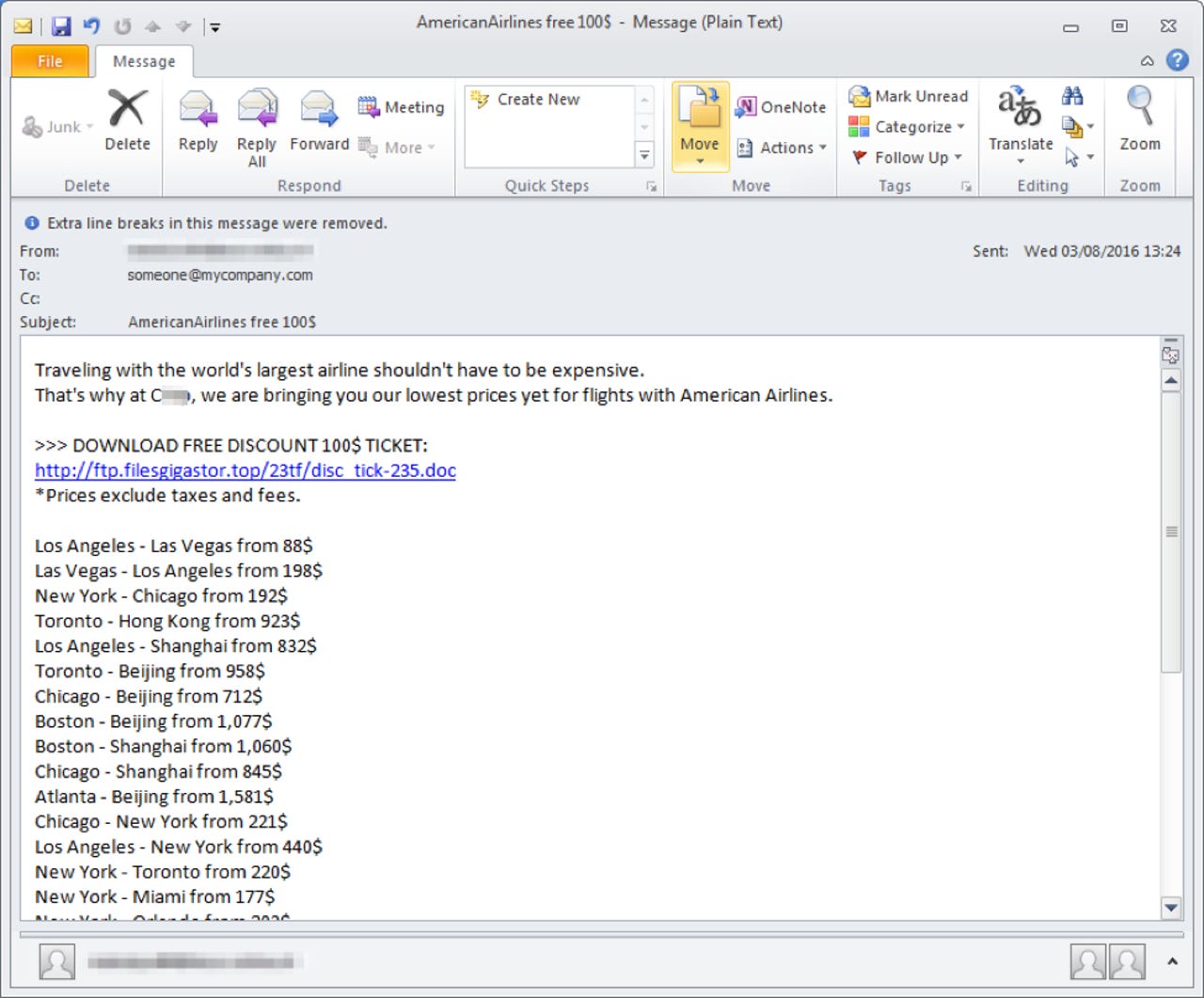
CryptFile2 lures victims with an offer of cheap flights.
A large-scale ransomware campaign is targeting US government agencies with hundreds of thousands of emails containing embedded malicious URLs, rather than the more common method of attaching infected files to the message.
When it was first discovered by cybersecurity researchers in March, the CryptFile2 ransomware campaign behaved like other pieces of malware, spreading via exploit kits downloaded in infected files. But now Proofpoint researchers have observed that the ongoing campaign has adapted its techniques, delivering ransomware via embedded URL links -- a degree of targeting not used before.
The new variant of CryptFile2 began appearing this month, using convincing-looking faked emails claiming to be from a legitimate travel website and offering deals on flights. But if a recipient clicks on the email link, they're directed to download Microsoft Word documents which then use social engineering techniques to trick the user into enabling malicious macros.
CryptFile2 attempting to trick a target into enabling malicious macros to install the ransomware.
Once these macros are enabled, the ransomware payload is downloaded, and hackers demand payment in Bitcoin order to unencrypt the infected system. In the ransom note, the cybercriminals say there's no other way to regain access to the locked files except by making the payment and also threaten to double the ransom if the payment doesn't come quickly.
Security
Previously spread by Nuclear and Nutrino exploit kits, the new variant of the CryptFile2 campaign began on 3 August with hundreds of thousands of messages sent to targets, with thousands of additional emails being sent each following day.
The campaign primarily targets state and local government agencies, although emails containing CryptFile2 have also been sent to education and healthcare providers.
The lack of an email attachment makes it easier for the malicious message to get past anti-malware and spam filters. "The targeting in this campaign, made possible through email distribution, brings increased risks to public sector organizations that may be less equipped to detect and mitigate these kinds of threats," Proofpoint said.
Cybersecurity researchers also warn that organisations that don't have the most up-to-date defences "may find themselves in the difficult position of having to pay the ransom, which carries its own set of risks" -- including not getting the files back, even if the ransom is paid.
A coalition of cybersecurity companies and law enforcement agencies recently teamed up to offer ransomware victims a means of getting their files back without having to give into the hackers' demands.