North Korea's history of bold cyber attacks

North Korea’s growing criminal cyberthreat
North Korean hackers, backed by the state, are believed to be responsible for an array of bold attacks made in the name of money, or the reputation of the Democratic People's Republic of Korea regime. Some of these include, but are not limited to...
SEE: Can Russian hackers be stopped? Here's why it might take 20 years (TechRepublic cover story) | download the PDF version
Nonghyup, 2011
An attack against South Korean farm co-op Nonghyup paralyzed the bank, leaving customers unable to access funds for over a week.
South Korean banks, 2013
The operations of three major banks and two broadcasters collapsed at the same time as North Korean news agency KNCA relayed a message from North Korean's leadership, pledging to destroy the South's government.
Sony, 2014
The FBI blamed North Korea for a brutal cyberattack on Sony which compromised the tech company's networks and led to the leak of terabytes of information online. It is believed the attack was launched in response to Sony's planned release of, The Interview, a film which tells the satirical story of journalists recruited to assassinate Kim Jong Un.
See also: Thousands could launch Sony-style cyberattack, says ex-hacker (CNET)
The Central Bank of Bangladesh, 2016
The notorious bank heist that targeted the Central Bank of Bangladesh's Federal Reserve account lead to the theft of $81 million, and was connected to the Sony breach -- and therefore North Korea -- through the malware utilized in the compromise of the SWIFT bank communications system.
WannaCry, 2017
The release of NSA tools -- including EternalBlue by the Shadow Brokers hacking group -- ultimately led to the global WannaCry ransomware attack, which debilitated companies worldwide without prejudice. It is believed that North Korea threat actors implemented the exploit in distributing the ransomware.
See also: WannaCry: The smart person's guide
US utilities, 2017
Cybersecurity firm FireEye believes that the rogue state is behind a number of attacks aimed at US electricity companies.
See also: North Korean Actors Spear Phish U.S. Electric Companies (FireEye)
Energy services, 2017
A group known as Covellite, connected to North Korea, has been linked to attacks against US, European and East Asian organizations involved in consumer energy. However, in recent months, attacks against US targets appear to have been abandoned.
Cryptocurrency exchanges, South Korea
South Korea is a common target for DPRK hackers, and cryptocurrency exchanges -- containing millions of dollars' worth of virtual assets -- are lucrative. According to South Korean officials, North Korea is responsible for the theft of "billions of won" from exchanges over the past 12 months.
Cryptojacking, worldwide
Cybersecurity professionals have suggested that the regime's hackers have created cryptojacking malware designed to steal victim CPU power to mine cryptocurrency. Proceeds are allegedly finding their way to North Korea's Kim Il Sung University.
See also: Inside the early days of North Korea's cyberwar factory
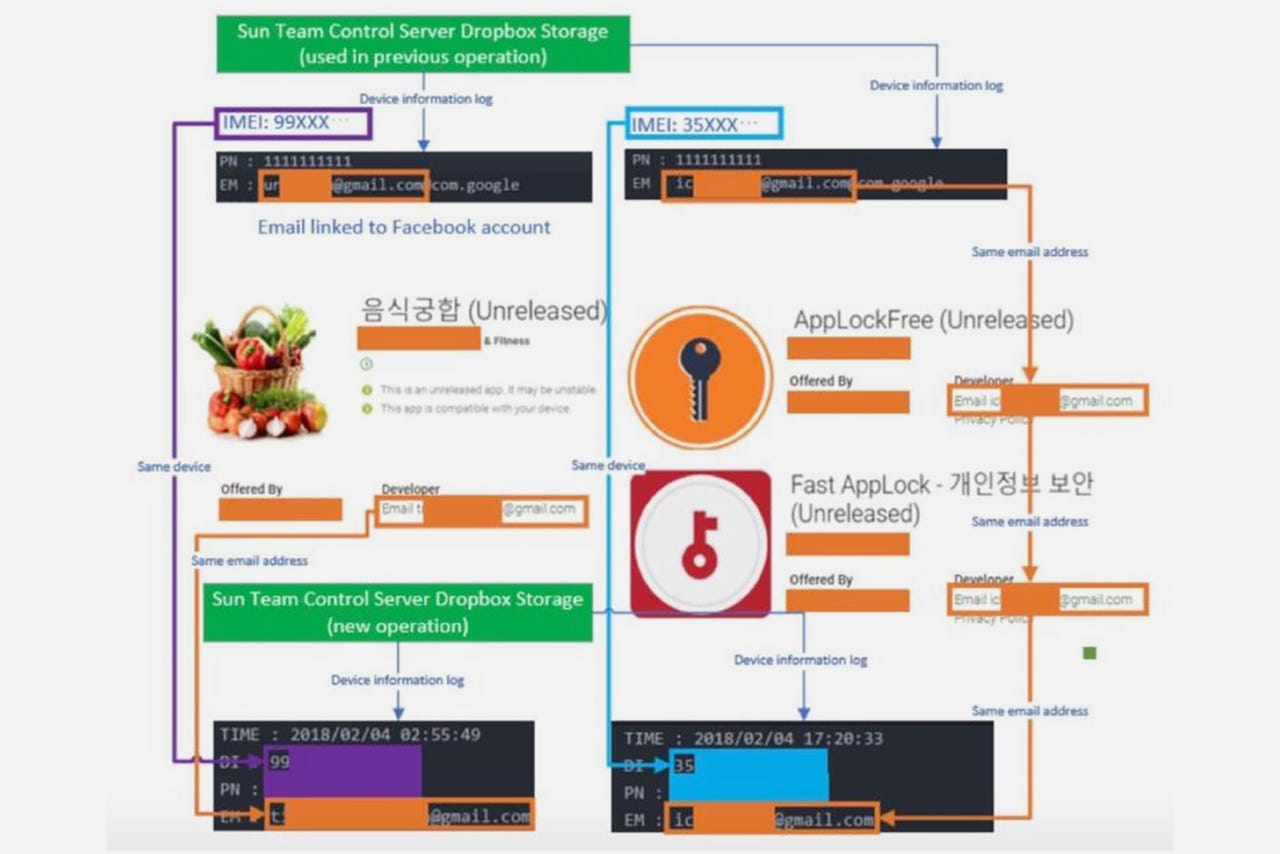
Journalists and defectors, worldwide
Malware-laden Android apps, aimed at North Korean defectors and journalists covering the regime, keep slipping through the net and appearing on Google Play.
Ontario's rail system, 2018
Metrolink, Ontario's transportation agency, claims that North Korea attempted to derail IT systems, without success.