Report: 48% of 22 million scanned computers infected with malware
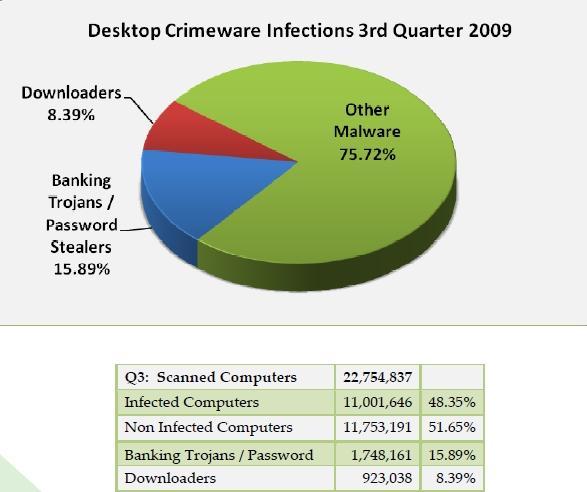
According to the report, the overall number of infected computers (page 10) used in the sample decreased compared to previous quarters, however, 48.35% of the 22,754,847 scanned computers remain infected with malware.
And despite that the crimeware/banking trojans infections slightly decreased from Q2, over a million and a half computers were infected.
More details:
"Though the scanning system checks for many different kinds of potentially unwanted software, for this report, Panda Labs has segmented out ‘Downloaders’ and ‘Banking Trojans/Password Stealers’ as they are most often associated with financial crimes such as automated phishing schemes.
The proportion of infected computers detected has decreased for the first time in 2009. In the same way, the proportion of banking Trojans has decreased from a 16.94 percent in Q2 to 15.89 percent in Q3. The proportion of Downloaders has dropped to 8.39 percent from 11.44 percent in Q2 ? but it is still higher than in Q1 (4.22%)."
With the sample itself limited to that of a particular vendor, the remaining over million and a half crimeware infected computers, remain a cause for concern.
- Related posts: Modern banker malware undermines two-factor authentication; Citizens Financial sued for insufficient E-Banking security; Commonwealth fined $100k for not mandating antivirus software; Standardizing the Money Mule Recruitment Process - learn how money mule recruitment works in order to avoid it
Due to its mass adoption, and lack of awareness building on its actual applicability in fighting today's crimeware, two-factor authentication is still perceived as highly effective authentication solution. Otherwise, why would financial institutions keep insisting on its usefulness? Things are thankfully heading in the right direction.
How does this happen, and how are cybercriminals bypassing the phone verification process?
- Malware sits inside a user's browser and waits for the user to log into a bank. During login, the malware copies the user's ID, password and OTP, sends them to the attacker and stops the browser from sending the login request to the bank's website, telling the user that the service is "temporarily unavailable." The fraudster immediately uses the user ID, password and OTP to log in and drain the user's accounts.
- Other malware overwrites transactions sent by a user (URLZone Trojan Network) to the online banking website with the criminal's own transactions. This overwrite happens behind the scenes so that the user does not see the revised transaction values. Similarly, many online banks will then communicate back to the user's browser the transaction details that need to be confirmed by the user with an OTP entry, but the malware will change the values seen by the user back to what the user originally entered. This way, neither the user nor the bank realizes that the data sent to the bank has been altered.
- Authentication that depends on out-of-band authentication using voice telephony is circumvented by a simple technique whereby the fraudster asks the phone carrier to forward the legitimate user's phone calls to the fraudster's phone. The fraudster simply tells the carrier the original phone number is having difficulty and needs the calls forwarded, and the carrier does not sufficiently verify the requestor's identity before executing the fraudster's request.
Last month, The American Bankers' Association (ABA) issued a similar warning to small businesses, recommending the use of dedicated PC for their E-banking activities, one which is never used to read email or visit web sites in an attempt to limit the possibility of crimeware infection.
No matter which adaptive approach you'd consider (Time to ditch Windows for online banking and shopping; Live CDs), cybercriminals have clearly adapted to the currently implemented multi-factor authentication processes in place.