How-to Guides
Practical tips, tricks, and advice for getting things doneAnalysis & Opinion
Explore a fresh perspectiveLatest
- Buy a 5-year subscription to AdGuard VPN for $40
- How to turn on Private DNS Mode on Android - and what it can do for you
- How do I use a VPN to watch the Olympics?
- What caused the great CrowdStrike-Windows meltdown of 2024? History has ...
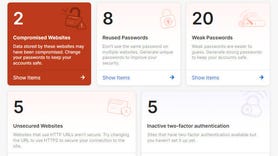
- 7 password rules to live by in 2024, according to security experts
-
In an X thread, the AI giant explains 'how we're prioritizing safety in our work.' Here's what's new.