Popular Dark Web hosting provider got hacked, 6,500 sites down

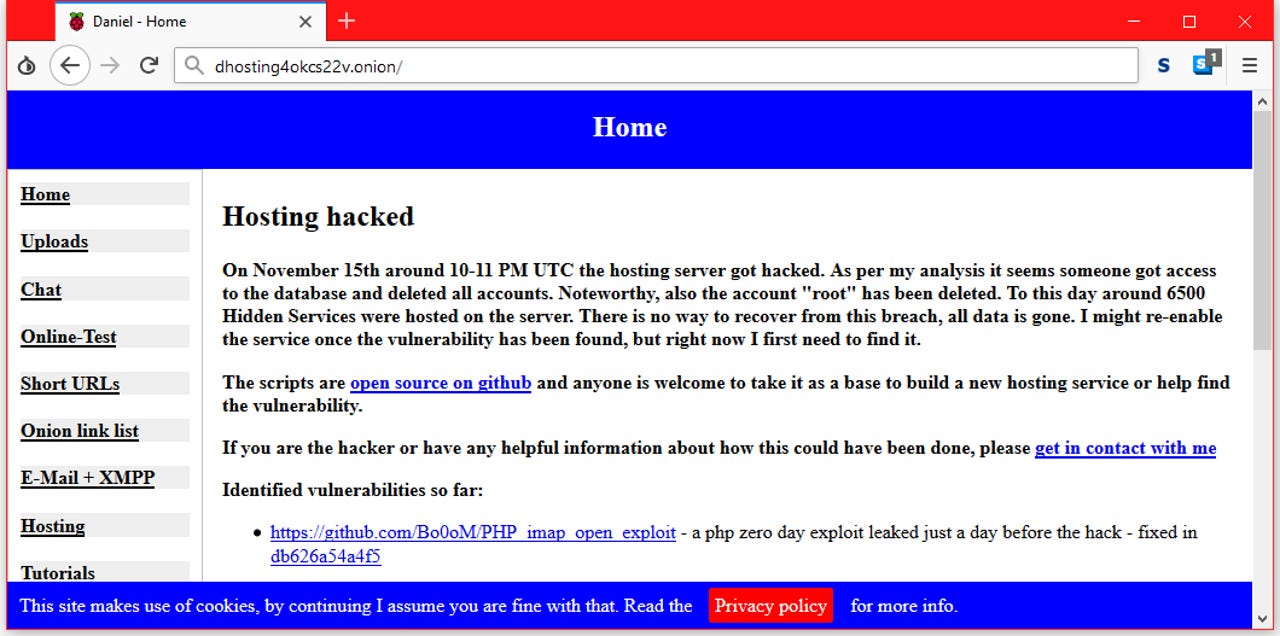
Daniel's Hosting, one of the largest providers of Dark Web hosting services, was hacked this week and taken offline, ZDNet has learned from one of our readers.
The hack took place on Thursday, November 15, according to Daniel Winzen, the software developer behind the hosting service.
"As per my analysis it seems someone got access to the database and deleted all accounts," he said in a message posted on the DH portal today.
Winzen said the server's root account was also deleted, and that all 6,500+ Dark Web services hosted on the platform are now gone.
"Unfortunately, all data is lost and per design, there are no backups," Winzen told ZDNet in an email today. "I will bring my hosting back up once the vulnerability has been identified and fixed."
"As of now I haven't been able to do a full analysis of the log files and need to further analyze them, but based on my findings so far I believe that the hacker has only been able to gain administrative database rights. There is no indication of having had full system access and some accounts and files that were not part of the hosting setup were left untouched," Winzen told us.
"I might re-enable the service once the vulnerability has been found, but right now I first need to find it," he added.
And for the past two days, Winzen has been doing just that, looking at possible vulnerabilities that the hacker might have exploited to gain access to his server.
Currently, he identified one flaw, a PHP zero-day vulnerability. Details about this unpatched vulnerability were known for about a month in Russian PHP programming circles, but the flaw gained a lot of attention among the wider programming and infosec communities, on November 14, a day before the hack.
But Winzen told ZDNet that he doesn't believe this to be the hacker's actual point of entry.
"It is a vulnerability reported as a possible point of entry by a user and my setup was, in fact, vulnerable," he told us. "However I would deem it as unlikely to have been the actual point of entry as the configuration files with database access details were read-only for the appropriate users and commands run by this vulnerability shouldn't have had the necessary permissions."
Until then, Winzen promised more updates on the DH portal as his investigation continues. The German developer also told ZDNet that the hack might also be "an opportunity to improve some bad design choices of the past and start with an all new and improved setup, which I expect to be able to provide in December."
After the Anonymous hacker collective breached and took down Freedom Hosting II, another popular Dark Web hosting provider, in February 2017, Daniel's Hosting became the largest hosting provider for Dark Web services.
The service has been used to host everything from malware operations to political blogs, and the list of suspects who might have been interested in hacking DH ranges accordingly, from rival cybercrime gangs to nation-state hackers looking to track down dissidents and political activists.
The hack might have also been facilitated by the fact that the DH service's source code has always been open-sourced on GitHub and might have provided attackers with a more broad look into the service's inner guts.
Cybercrime and malware, 2019 predictions
More security news:
- French police officer caught selling confidential police data on the dark webhttps://www.zdnet.com/article/aws-rolls-out-new-security-feature-to-prevent-accidental-s3-data-leaks/
- AWS rolls out new security feature to prevent accidental S3 data leaks
- Zero-day in popular WordPress plugin exploited in the wild to take over sites
- Access data for 70% of top US & EU websites sold on the dark web TechRepublic
- Most ATMs can be hacked in under 20 minutes
- Researchers find stolen military drone secrets for sale on the dark web CNET
- DOD disables file sharing service due to 'security risks'
- Card skimming malware removed from Infowars online store
Best Black Friday 2018 deals:
- Amazon Seven Days of Black Friday Deals: All-time lows on office devices
- Amazon Black Friday 2018 deals: See early sales on Echo, Fire HD
- Best Buy Black Friday 2018 deals: Deep discounts on Apple Mac, Microsoft Surface
- Target Black Friday 2018 deals: $250 iPad mini 4, $120 Chromebook
- Walmart Black Friday 2018 deals: $99 Chromebook, $89 Windows 2-in-1
- Dell Black Friday 2018 deals: $120 Inspiron laptop, $500 gaming desktop
- Newegg Black Friday 2018 deals: $50 off Moto G6, $70 off Nest thermostat
- Office Depot Black Friday 2018 deals: $300 off Lenovo Flex, $129 HP Chromebook
- eBay Black Friday 2018 deals: See early sales on Galaxy Watch, Chromecast
- Lenovo Black Friday 2018 deals: ThinkPad laptops and more
- Microsoft Store Black Friday 2018 deals: Ad showcases Surface, laptop deals
- Windows laptops Black Friday deals: Dell, HP, Lenovo
- Chromebook Black Friday 2018 deals: Dell, Google, HP
- Best tablet Black Friday deals: Apple iPad, Amazon Fire
- Black Friday 2018 iPhone deals: $400 iPhone X gift card, BOGO iPhone XR
- Black Friday 2018 smartphone deals: OnePlus 6T, LG G7