AWS rolls out new security feature to prevent accidental S3 data leaks

Amazon's Web Services division has rolled out new security features to AWS account owners today that are meant to prevent accidental data exposures caused by the misconfiguration of S3 data storage buckets.
Security
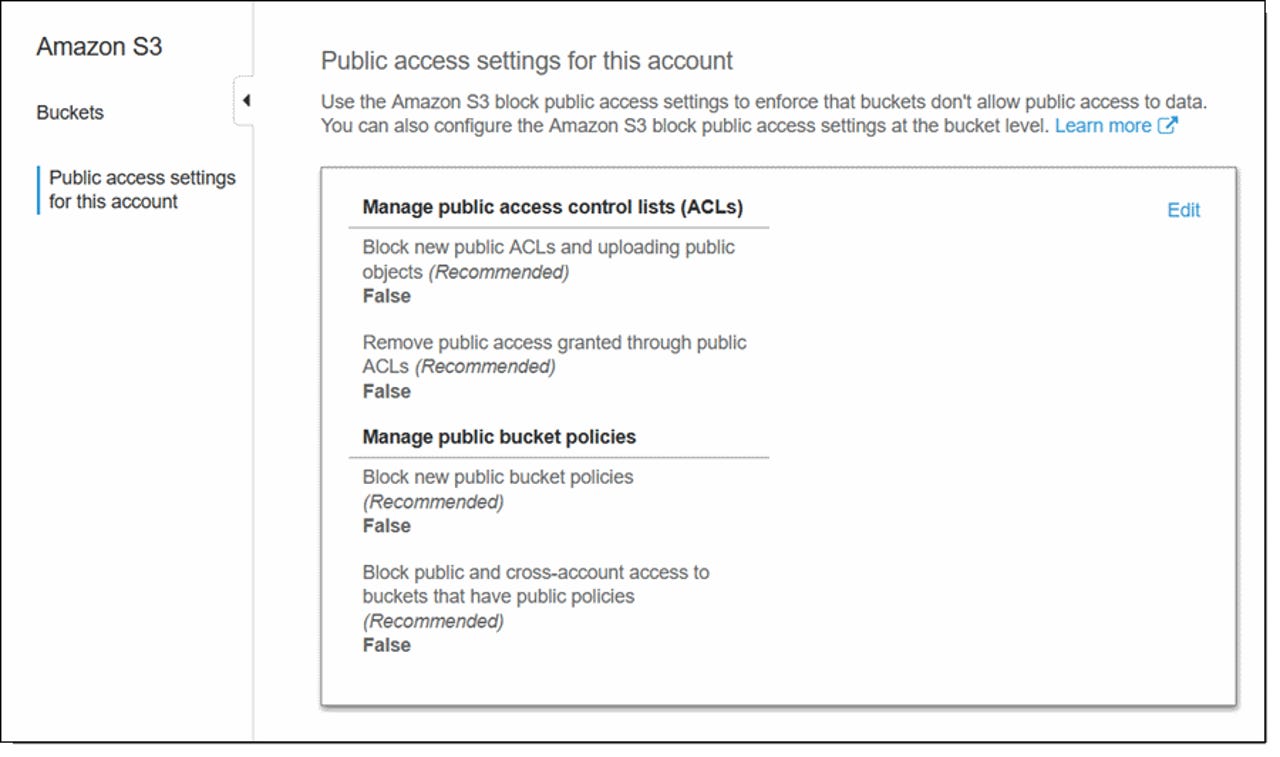
Starting today, AWS account owners will have access to four new options inside their S3 dashboards under the "Public access settings for this account" section.
These four new options allow the account owner to set a default access setting for all of an account's S3 buckets. These new account-level settings will override any existing or newly created bucket-level ACLs (access control lists) and policies.
ZDNet: Black Friday 2018 deals: Business Bargain Hunter's top picks | Cyber Monday 2018 deals: Business Bargain Hunter's top picks
Account owners will have the ability to apply these new settings for S3 buckets that will be created from now onwards, to apply the new setting retroactively, or both.
Jeff Barr, Chief Evangelist for Amazon Web Services, said the new settings are meant to work as a master switch that prevents account owners or their employees/developers from accidentally opening S3 buckets and their data to the public by coding or misconfiguration errors at the app/bucket level.
These types of accidents (of misconfiguring S3 buckets) have been a major problem for AWS customers for the past few years, and a serious black eye for AWS itself. Many cyber-security experts have considered that Amazon did not do enough to warn AWS users about the dangers of exposing an S3 bucket or providing controls to prevent this from happening.
Amazon did act, in November last year, when it began displaying bright orange warnings in the AWS dashboard, next to each S3 bucket that allowed public access.
Today's updates come to address most of the criticism that the company has faced recently, and this update will provide the much-needed settings to prevent misconfiguration from exposing buckets, and not just tell account owners after they've already happened.
Just to put things in perspective and show how problematic the issue of accidental S3 bucket exposures has been, below is a (very incomplete) list of data breaches and data leaks that have been caused by a company or app that ran a misconfigured S3 bucket that allowed anyone to view its content and not just the server owner.
- An unsecured S3 server exposed thousands of FedEx customer records
- An AWS S3 error exposed GoDaddy business secrets
- Accenture left a huge trove of highly sensitive data, including "keys to the kingdom," on exposed servers
- Customer records for at least 14 million Verizon subscribers, including phone numbers and account PINs, were exposed via an S3 bucket
- A Verizon AWS S3 bucket containing over 100 MB of data about the company's internal billing system was also found exposed online
- An S3 database left exposed leaked the personal details of job applications that had Top Secret government clearance
- Another S3 server exposed the details of 198 million American voters
- National Credit Federation leaked US citizen data through unsecured AWS bucket
- Nigerian airline Arik Air also leaked customer data via an exposed S3 bucket
- Pocket iNet ISP exposed 73GB of data including secret keys, plain text passwords
- An S3 leak at Alteryx left 123 million American households exposed to fraud and spam
- AgentRun, an insurance startup, also leaked sensitive customer health data via amisconfigured Amazon S3 bucket
- Donald Trump's campaign website also leaked intern resumes via an S3 bucket
- Spyware firm SpyFone also left customer data, recordings exposed online via an S3 server
- Booz Allen Hamilton, a top DOD contractor, leaked 60,000 files, including employee security credentials and passwords to a US government system
- An AWS S3 server leaked the personal details of over three million WWE fans who registered on the company's sites
- An auto-tracking company leaked over a half of a million car and car owner details.
- Voting machine firm Election Systems & Software (ES&S) left an S3 bucket exposed online that contained the personal records of 1.8 million Chicago voters
- Dow Jones leaked the personal details of 2.2 million customers
- An S3 bucket leaked data of thousands of Australian government and bank employees
- Password manager Keeper also exposed an S3 server
According to research published last year, Skyhigh Networks (now part of McAfee) found that around seven percent of all AWS S3 buckets were publicly exposed.
In addition to the new AWS S3 public access settings, Amazon also announced major news for DynamoDB, a high-load database engine, also part of the AWS suite. Starting today, Amazon said all data stored inside DynamoDBs will be encrypted by default.
"You do not have to make any code or application modifications to encrypt your data," Amazon said in a press release. "DynamoDB handles the encryption and decryption of your data transparently and continues to deliver the same single-digit millisecond latency that you have come to expect."
These were 2017's biggest hacks, leaks, and data breaches
Related coverage:
- ATM jackpotting attacks hit the US TechRepublic
- DOD disables file sharing service due to 'security risks'
- Many free mobile VPN apps are based in China or have Chinese ownership
- Dutch government report says Microsoft Office telemetry collection breaks GDPR
- You can soon take out cash from PayPal at Walmart CNET
- One in five Magecart-infected stores get reinfected within days
- Card skimming malware removed from Infowars online store
- Most ATMs can be hacked in under 20 minutes
Best Black Friday 2018 deals:
- Amazon Seven Days of Black Friday Deals: All-time lows on office devices
- Amazon Black Friday 2018 deals: See early sales on Echo, Fire HD
- Best Buy Black Friday 2018 deals: Deep discounts on Apple Mac, Microsoft Surface
- Target Black Friday 2018 deals: $250 iPad mini 4, $120 Chromebook
- Walmart Black Friday 2018 deals: $99 Chromebook, $89 Windows 2-in-1
- Dell Black Friday 2018 deals: $120 Inspiron laptop, $500 gaming desktop
- Newegg Black Friday 2018 deals: $50 off Moto G6, $70 off Nest thermostat
- Office Depot Black Friday 2018 deals: $300 off Lenovo Flex, $129 HP Chromebook
- eBay Black Friday 2018 deals: See early sales on Galaxy Watch, Chromecast
- Lenovo Black Friday 2018 deals: ThinkPad laptops and more
- Microsoft Store Black Friday 2018 deals: Ad showcases Surface, laptop deals
- Windows laptops Black Friday deals: Dell, HP, Lenovo
- Chromebook Black Friday 2018 deals: Dell, Google, HP
- Best tablet Black Friday deals: Apple iPad, Amazon Fire
- Black Friday 2018 iPhone deals: $400 iPhone X gift card, BOGO iPhone XR
- Black Friday 2018 smartphone deals: OnePlus 6T, LG G7